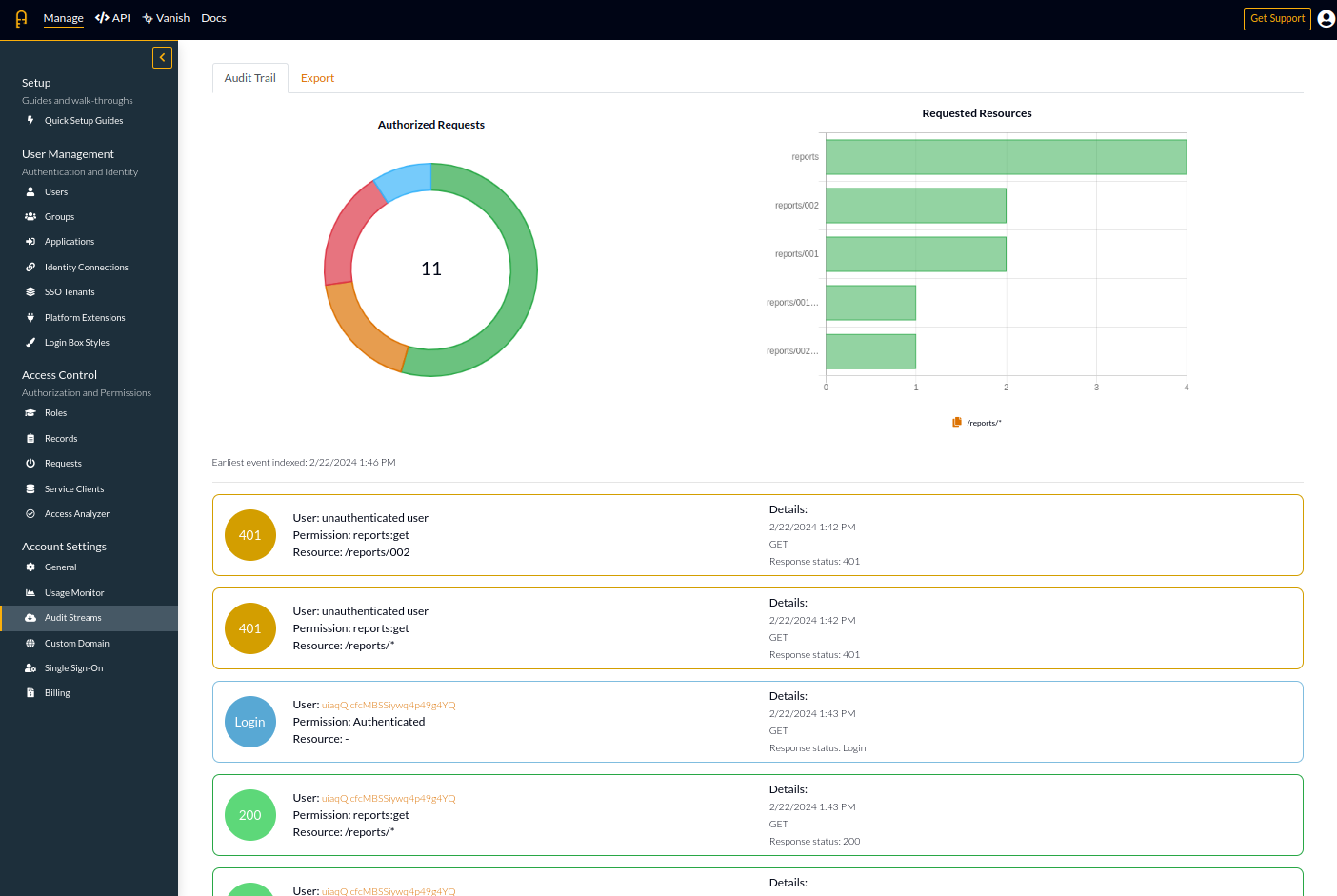
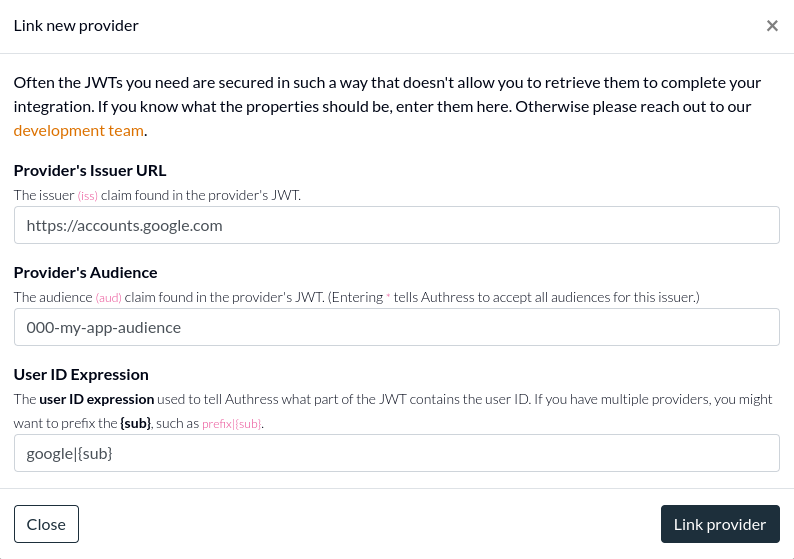
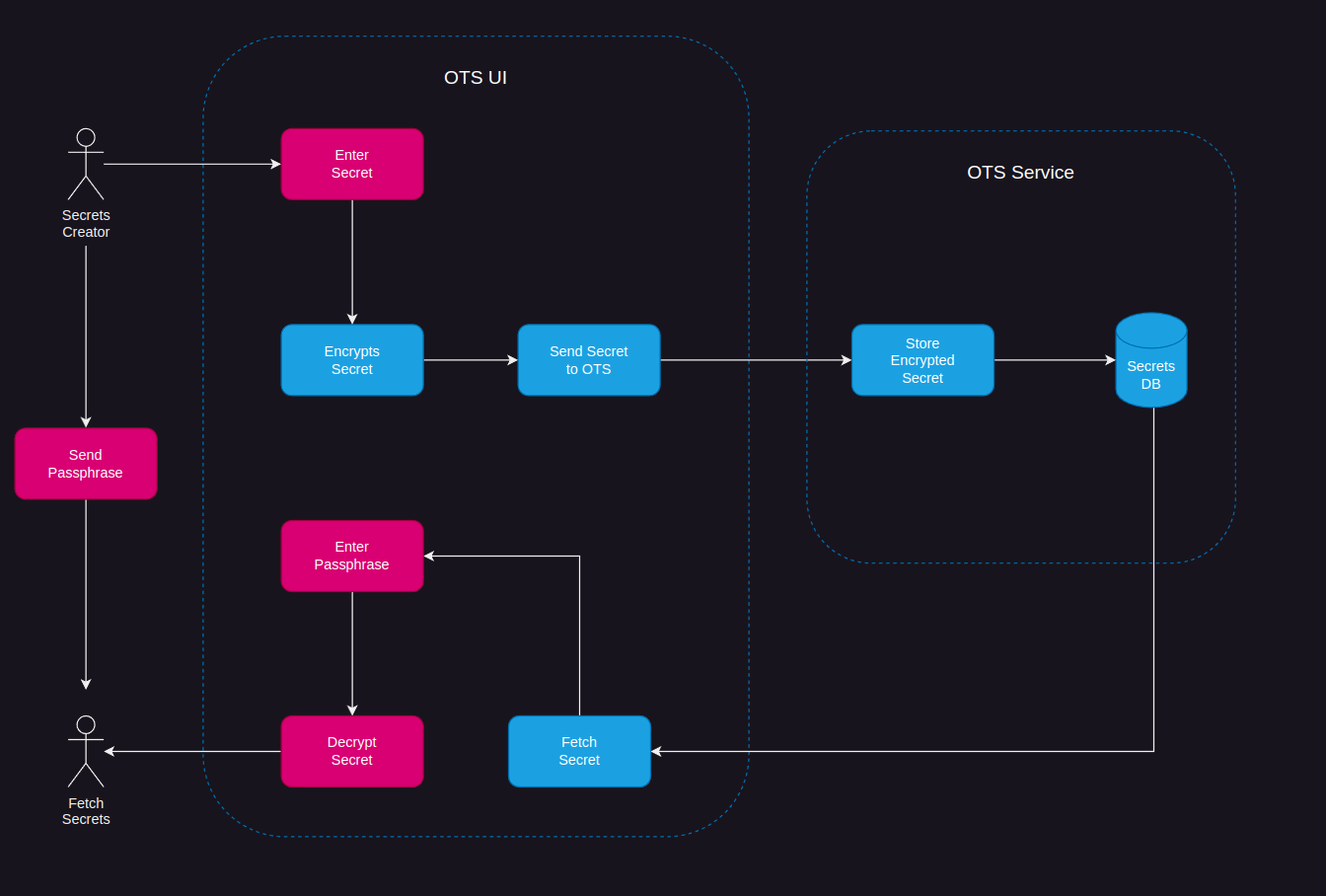
Tenant Selection
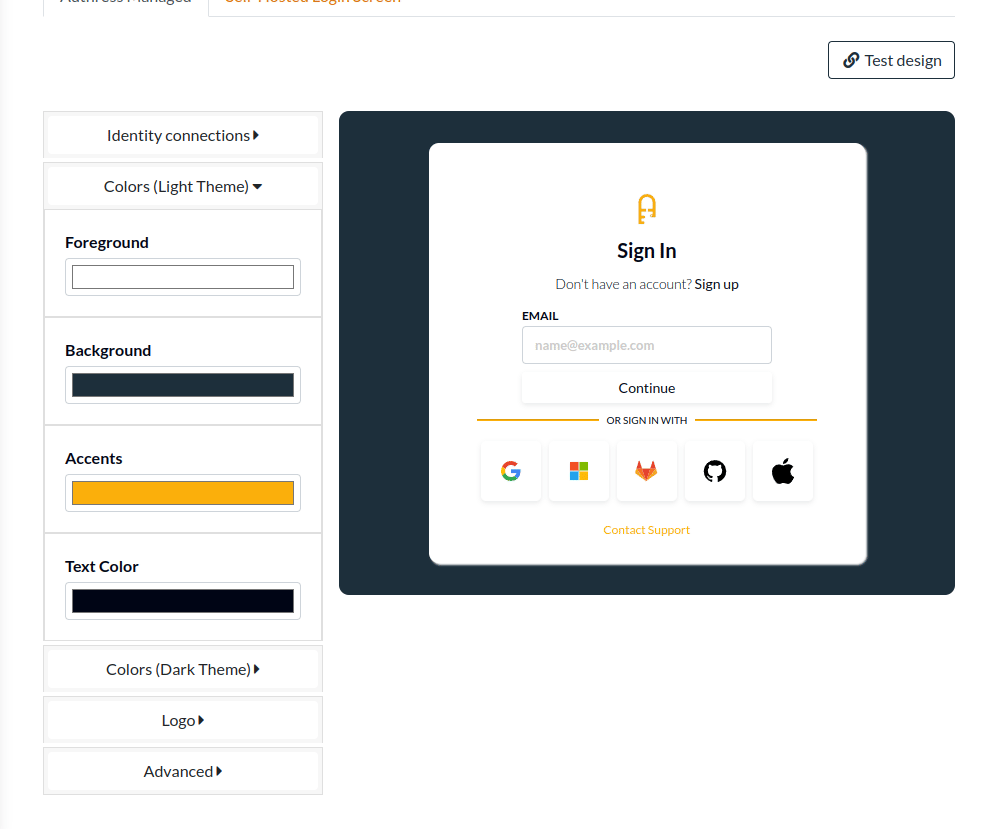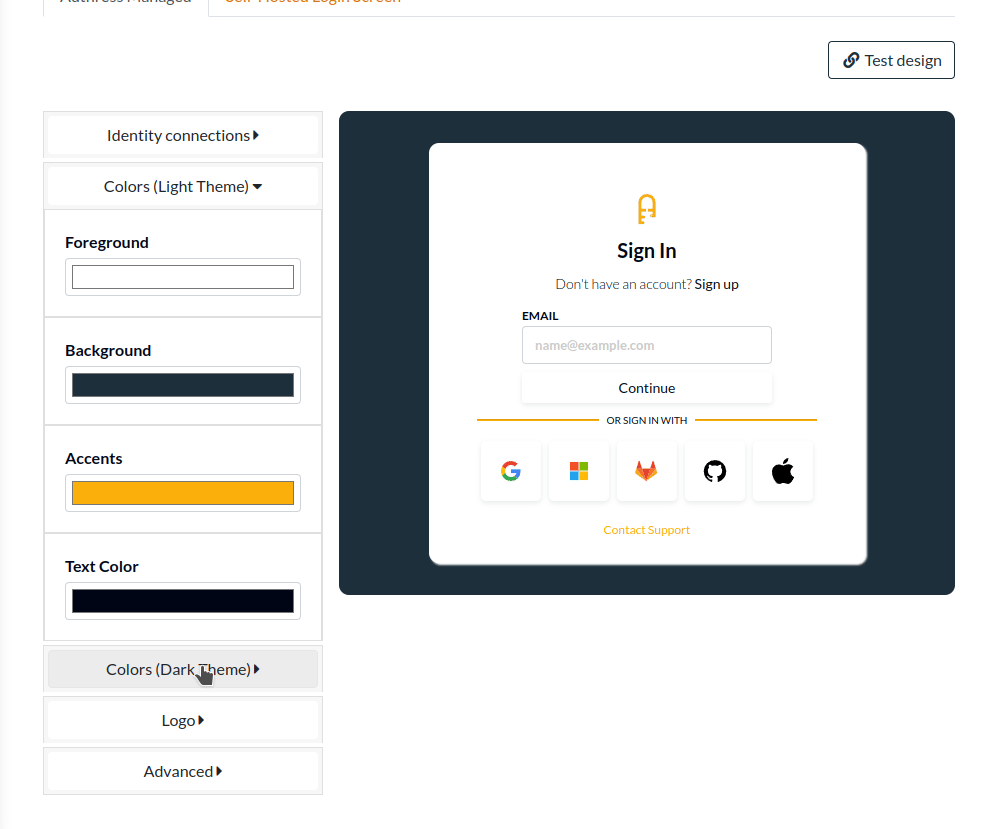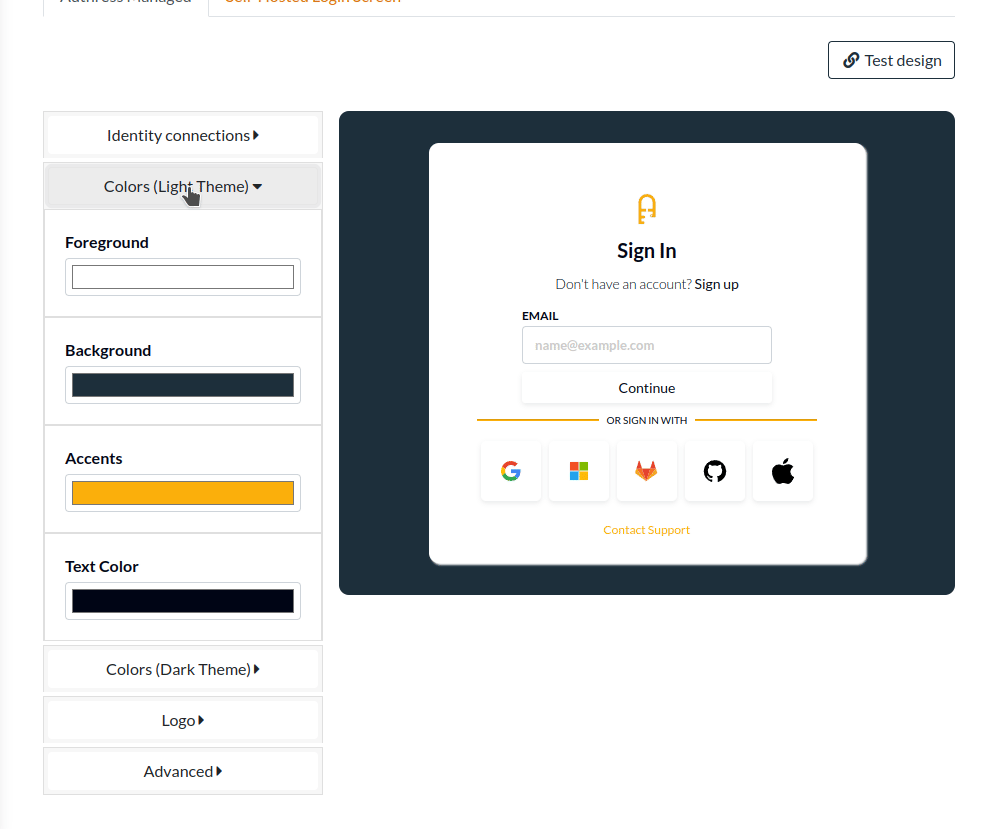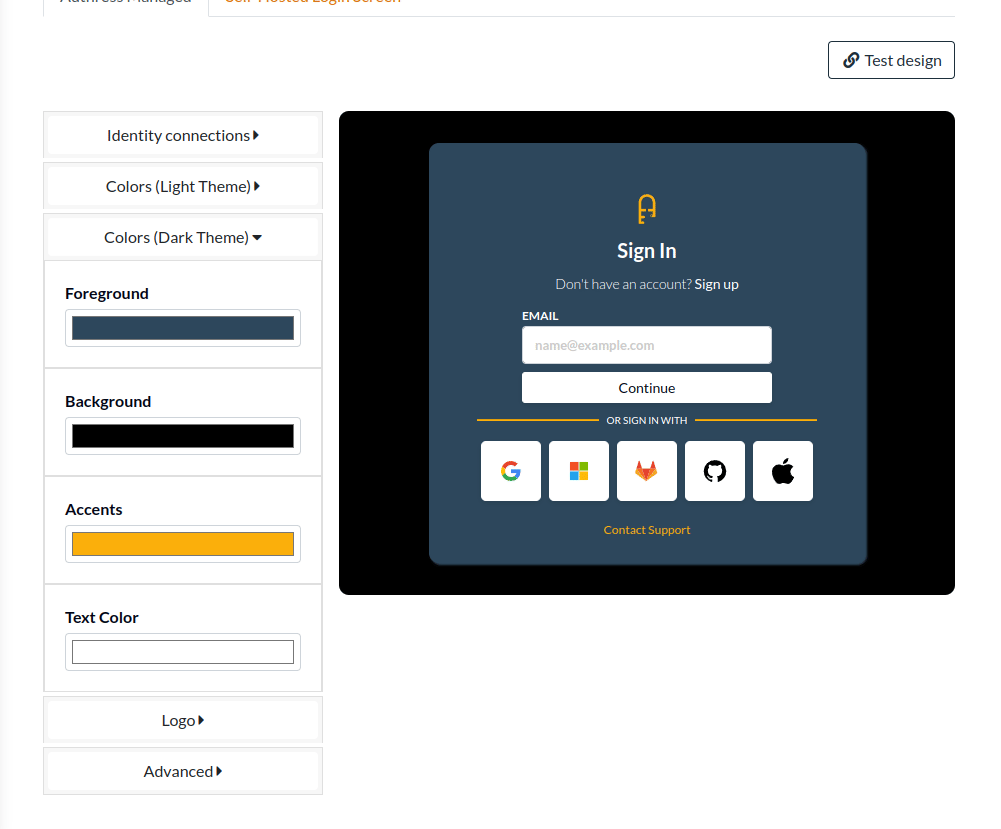
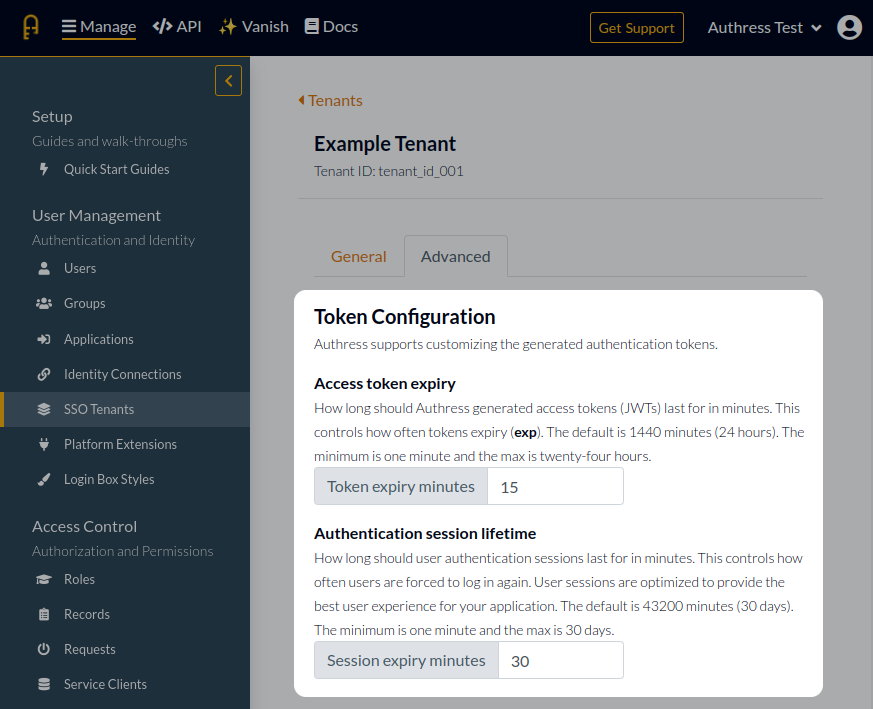
Authress Tenants exist to group users together to improve the login experience for your users. Users from the same company or business unit will often have SSO setup. To give users a seamless SSO login experience, the correct configuration must be provided. This configuration is specified in the Authress Tenant connection resource.
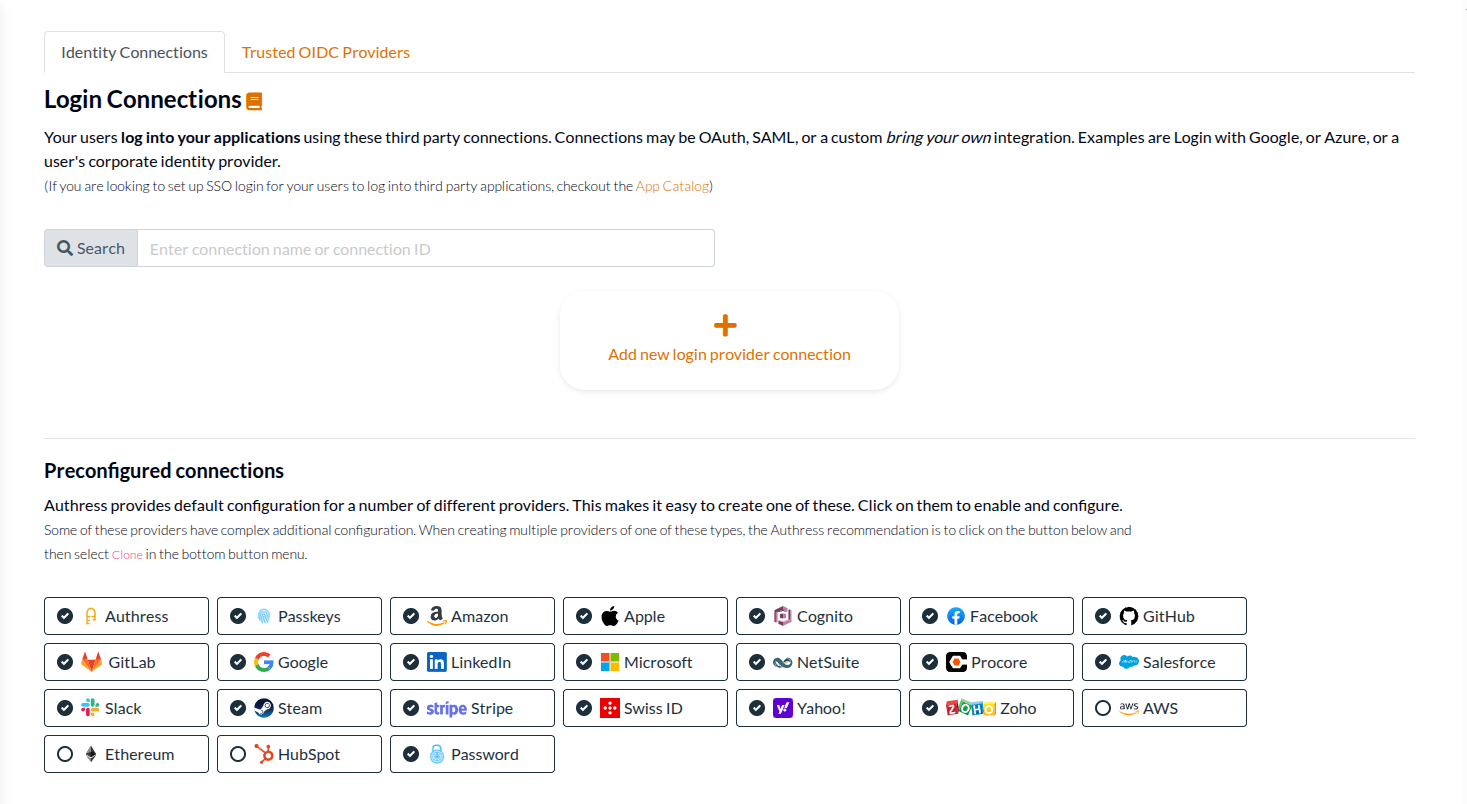
In some cases however, and usually when a company has not yet logged into your solution before, a tenant might not exist yet. An example might be if you have configured the Google or Microsoft Entra connections. In these cases, a user can log in with their SSO corporate identity provider without first configuring a tenant in your Authress account.
In those cases, Authress now provides a way to capture their tenant configuration and automatically generate a tenant resource with the appropriate configuration. That generated tenant will be assigned to the user and available in the user's generated tokens in the aud claim. See Tenants for more information.
Configuration
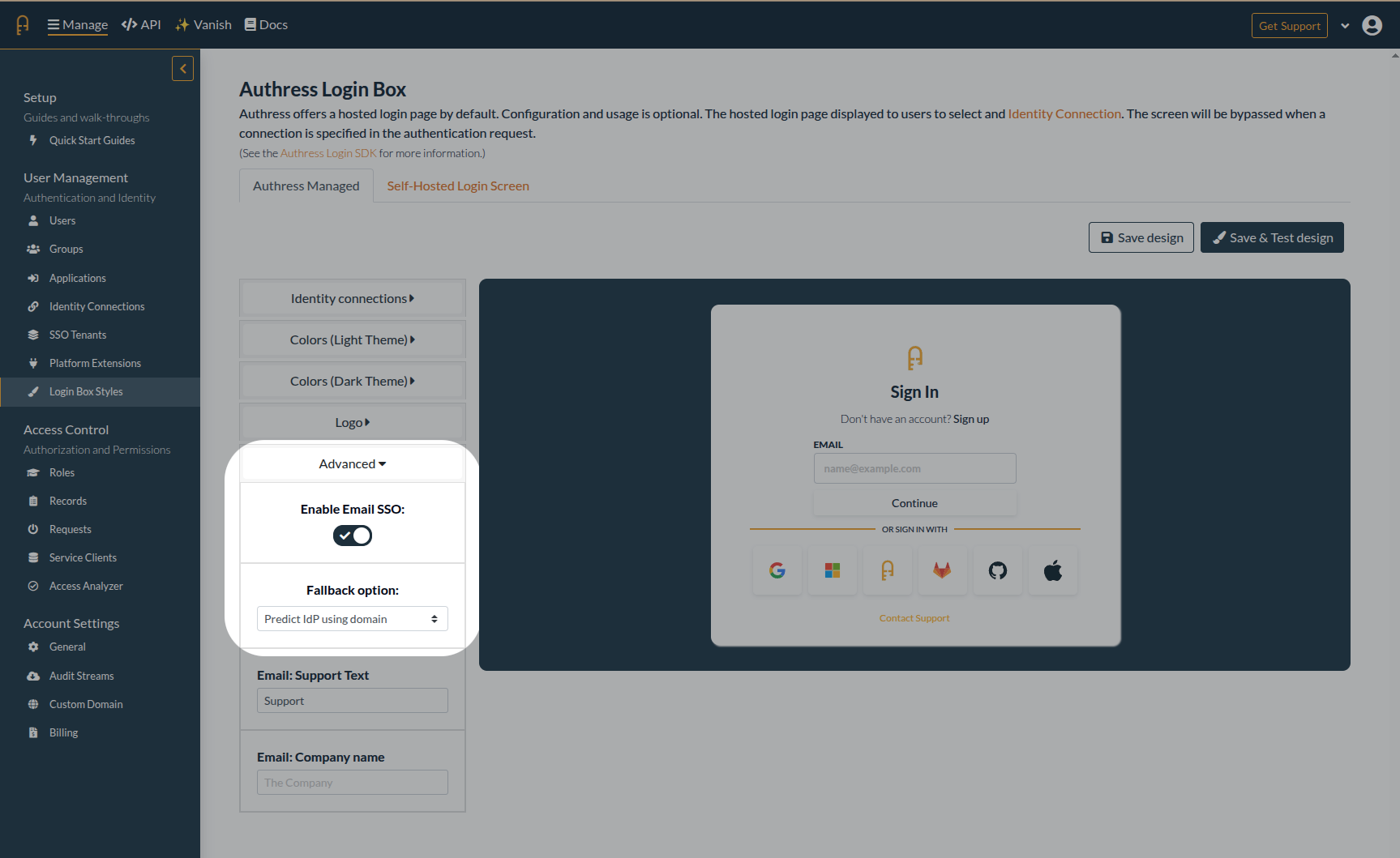
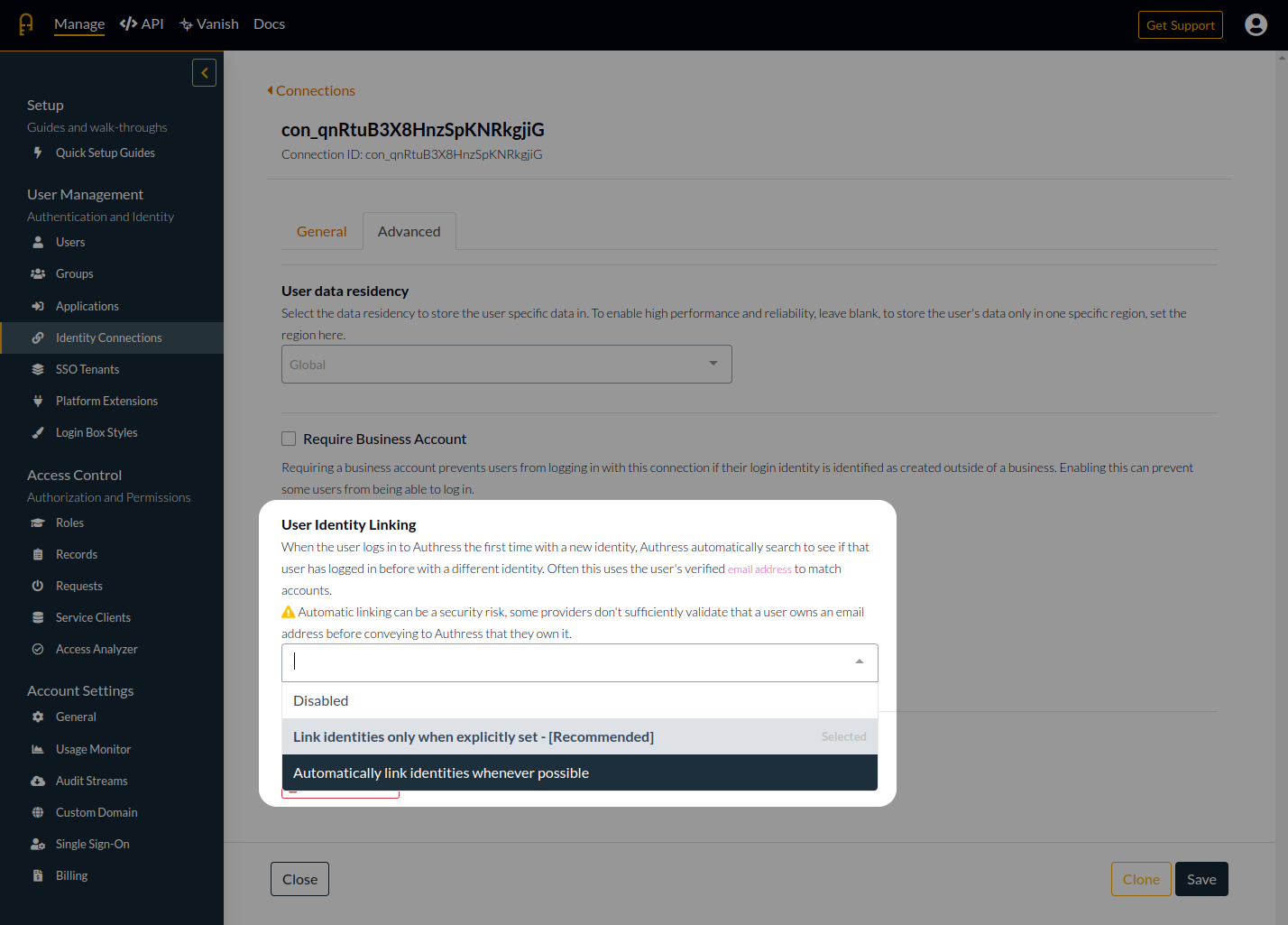
The default configuration in Authress is to not automatically generate a tenant. The automatic generation of resources can cause confusion and add noise to accounts. That being said, there are scenarios where it would be valuable to have the generated tenant automatically. To set this up, specify the Tenant Configuration for the relevant connection. To use the tenant specified by the identity provider, select Passthrough as the tenant assignment option.
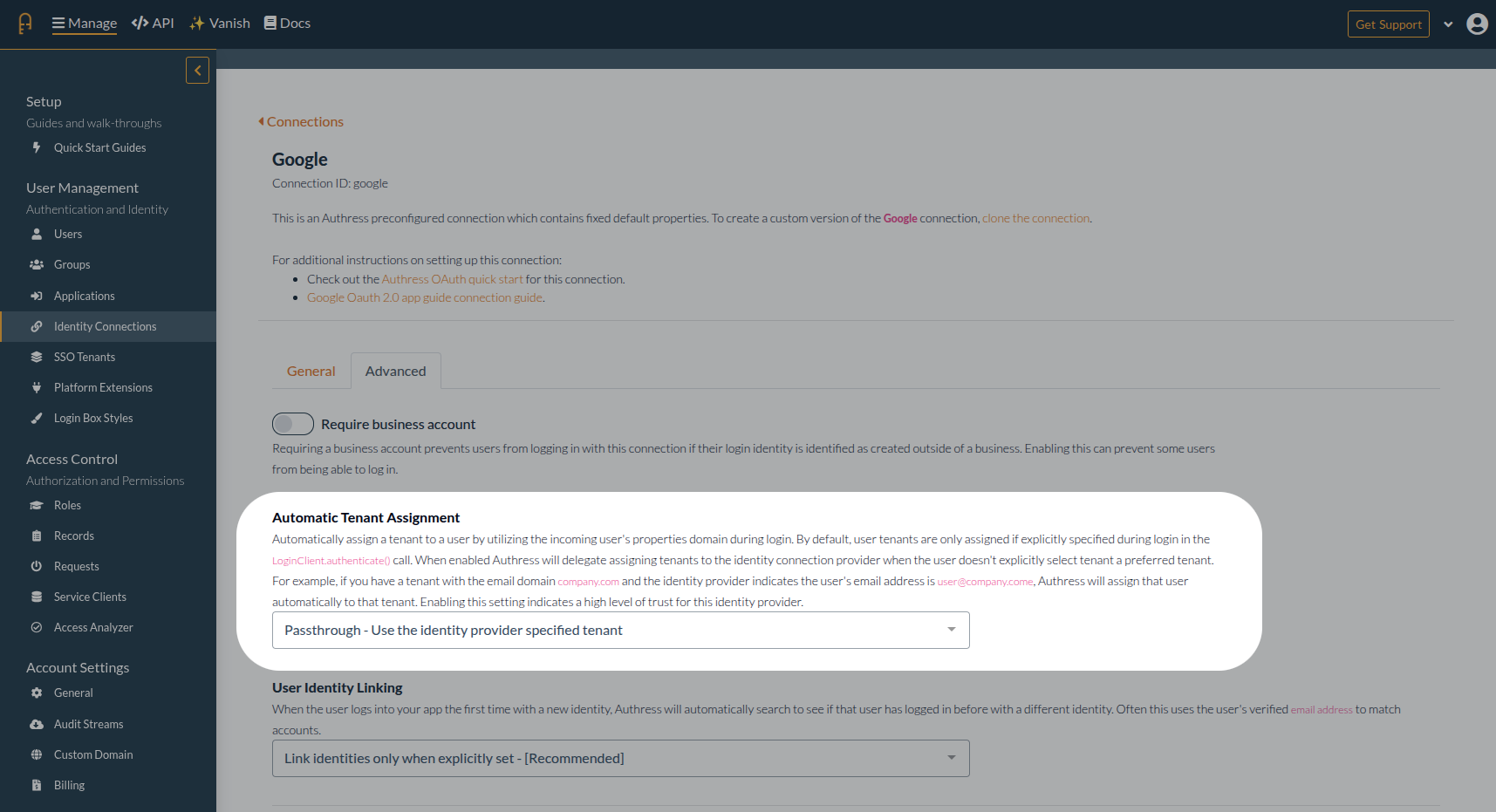
Example
To see how Passthrough tenant assignment might work in practice, consider a user associated with a Google Workspace account. In their account their Workspace Tenant defined by the HD property from Google Login, will be populated with their domain:
{
"iss": "https://accounts.google.com",
"aud": "1234567890-123456789abcdef.apps.googleusercontent.com",
"sub": "12345678901234567890",
"exp": 1745365295,
"name": "Example user",
"given_name": "Example",
"family_name": "User",
"hd": "example.com"
}
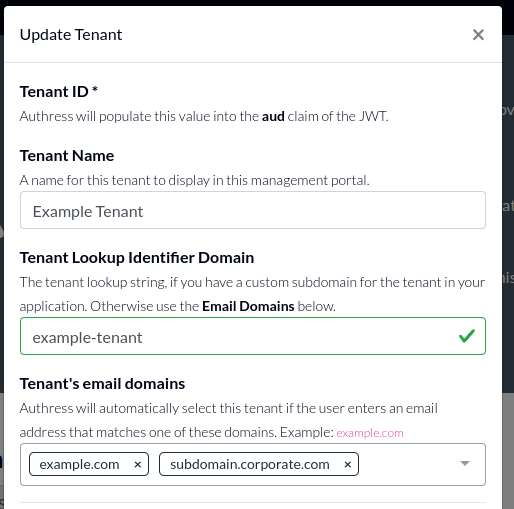
Once this user has completed login, a new tenant will be created:
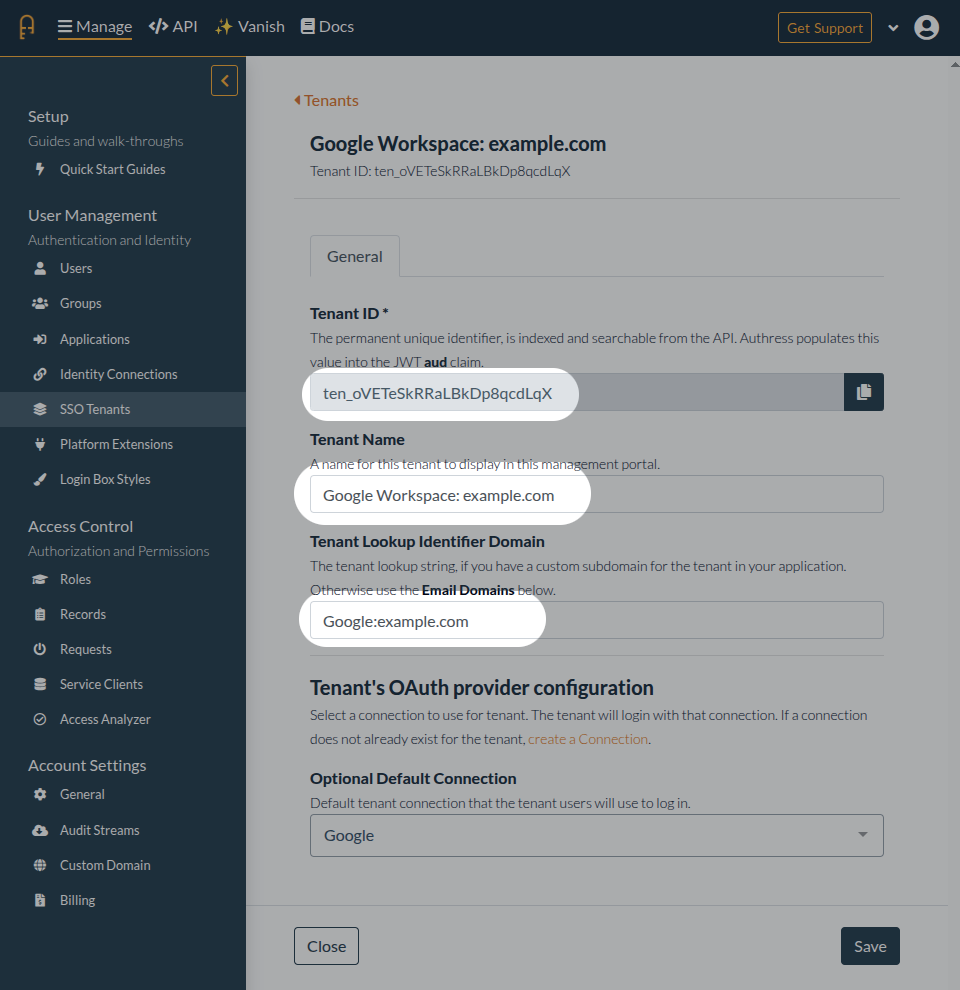
Additionally, all subsequent users from the same organization will also get assigned to the same tenant.