User Authentication and Login
General Login Features
Authress provides fundamentally a way for your users to log in using any strategy they want. Usually this means one of:
- A federated social provider
- OpenID, OAuth2, SAML, or other standards
- A direct account integration or passwordless using FIDO2 via WebAuthN
- SSO via their corporate identity provider
- OIDC, token exchanges, and machine identities
- Passkeys
Or one of these less common ones:
- Email and password
- Workload identities
- SCIM and IdP syncing
- Active Directory, and other ticket based systems
- Log in via a magic link (email, SMS, etc...)
- Custom auth flows via callback
Authress supports all of these, including MFA flows and all the usually necessities of user login. And while some of these are not as recommended as others, you get the complete set with Authress.
Authress also enables your customers to create applications than can utilize your platform as a login mechanism for their software. In Authress that is called creating a Platform Extension.
Login Configuration
To configure login using Authress, start by following the general setup guide for enabling identity provider authentication. After doing so your users will be able to log in using an Authress hosted login screen or a custom one:
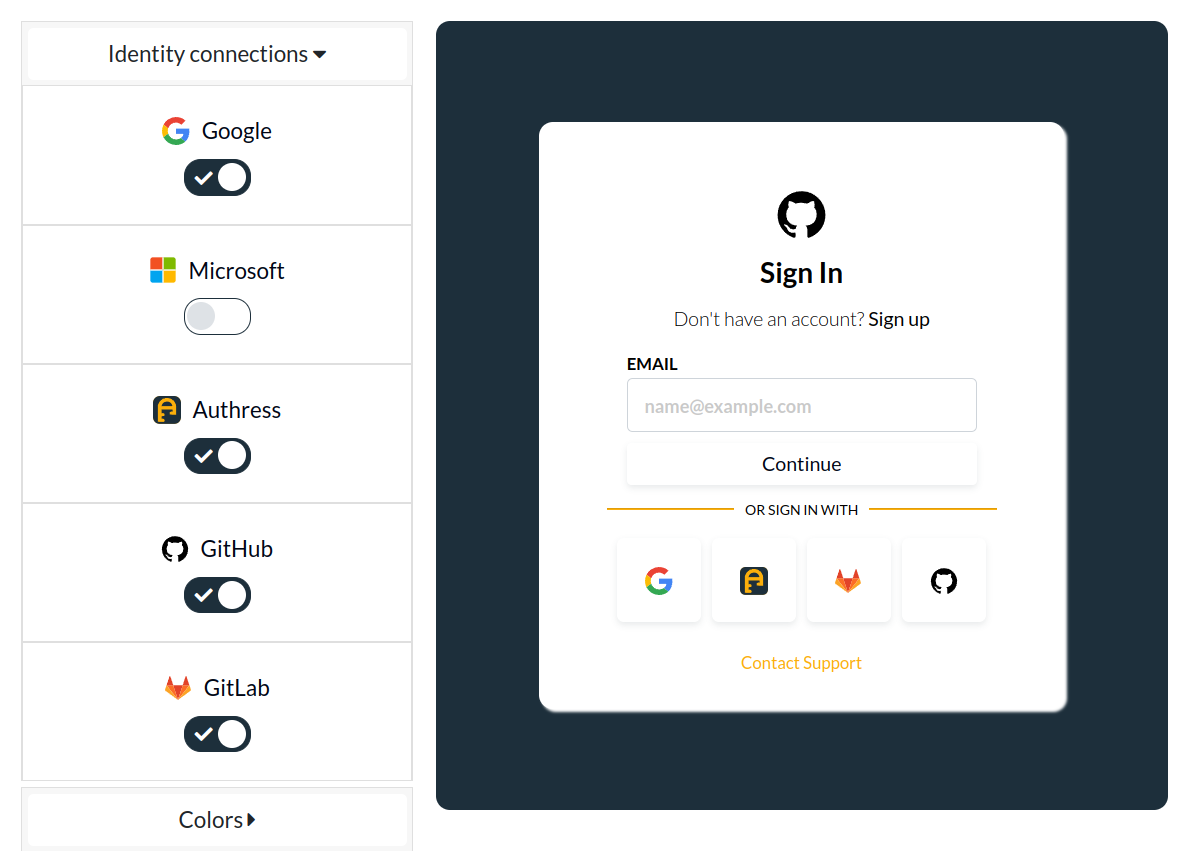
The customized login screen is dynamically generated from account configuration. And allows further customization based on:
- User Dark mode preferences
- Identity Connections
- Your company brand
- Customer SSO domains
- Plus additional customization options.
API authentication
Alternatively, if you looking for how to configure machine clients or add API keys and configure security your existing API endpoints, see the API authentication guide.
Tenants
Your users' accounts each are grouped into the tenant they belong to. When a customer signs up, you have the opportunity to create a new Authress Tenant. Each Tenant represents a different customer, and each tenant can have its own dedicated SSO login strategy. While most tenants will use one of the common login mechanisms, some will will bring their own corporate IdP. Tenants provides the way to identify and secure these login mechanisms within Authress.
Specifically, when a new tenant is created, the customer owner can also create a new Authress Identity Connection which stores the configuration that tenant needs to log in. Each tenant can have its own strategy for authentication. For how to configure tenants and custom user SSO, see Tenants and organization management.
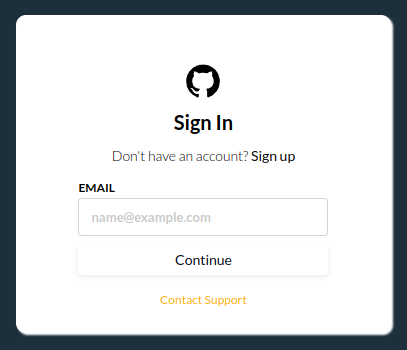
Depending on your configuration and the user's corporate SSO setup, this will be the default user sign in experience. This is a global configurable screen that enables you to pick your preferred connections and let the user enter their SSO domain. Depending on your customer's preferred integration options you can enable this dialog to fix your needs. With this users can successfully log into your platform directly.
Multifactor and Passkey support
For situations where a single factor authentication is not enough or a user's federated identify provider is not sufficient for the security of your application, you can add multifactor support. Authress supports adding a multifactor hardware or software device to any connection. That means, even for social connections, a hardware device such as a YubiKey can be added to the user's account to require an additional level before completing authentication.
Users can add any number of security keys to their account:
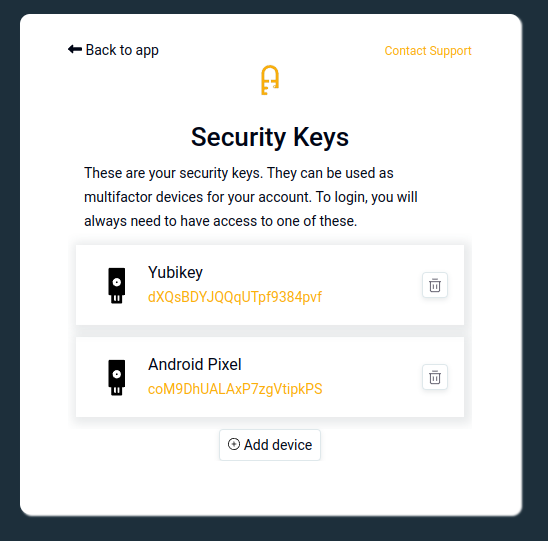
Then, during their login attempt they'll be automatically asked to provide their key.
Configuring user security keys
To configure user keys, redirect a login user to the Security Keys page:
import { LoginClient, UserConfigurationScreen } from '@authress/login';
const loginClient = new LoginClient({ authenticationServiceUrl: 'https://auth.yourdomain.com' });
await loginClient.openUserConfigurationScreen({
redirectUrl: window.location.href,
startPage: UserConfigurationScreen.MFA
});
🗃️ Login Box customizations
Step by step instructions for creating low-code and no-code user management and login box customizations.
📄️ Device Authenticators
Adding Multifactor Authenticators to your application such as Google Authenticator, TOTP, and Yubikeys.
📄️ Sessions
How secure user login persistence, authentication sessions, silent authentication, and users stay authenticated even when their access token expires.
📄️ Data residencies
Specify the data residency for your users' data storage on a per Identity Connection Provider (IdP).