Spotlight

How when AWS was down, we were not
Nothing can have an unlimited uptime. But even when AWS and other hyperscalers are having incidents, we've created an architecture that is resilient to those outages. Here's how we do it for Authress.

Securing CI/CD Access to AWS
Inevitably you'll need to secure the access from your CI/CD platform to your AWS or other cloud provider accounts. Here's how we do it at Authress.
Forget the checkboxes, make your security BLISS
BLISS is a framework that embodies a pragmatic approach to security. Traditionally, security is either all about defense and creating obstacles, or about ticking compliance checkboxes. It doesn't have to be this way.

Your security team’s job is not security
Sometimes your CISO and security team impose annoying rules on the development team. Sometimes these rules may seem at odds with security. There is a reason why that happens.

Your source code is not that special
Whenever the topic of protecting developer machines comes up, I inevitably hear that we must protect the machines in order to protect the source code. It's a fallacy. Your source code is really not that special.
Auth situation report
Before adding auth to your project, there is a lot to consider. The auth space is currently very active, with new vendors appearing and old ones repositioning themselves. How to pick the right one? What to search for? What are the common pitfalls? Read to find out.
To authenticate or to authorize - what is the difference?
Authentication vs authorization - which one is which? Even experienced software developers confuse the two. Let’s make it crystal clear once and for all - what is the difference and why it matters.
So you want to build your own authorization?
When writing new software, it's hard to notice complexity creeping in. Authorization is one of the aspects where things start deceptively simple and before you notice, you end up in a zoombombing scandal.
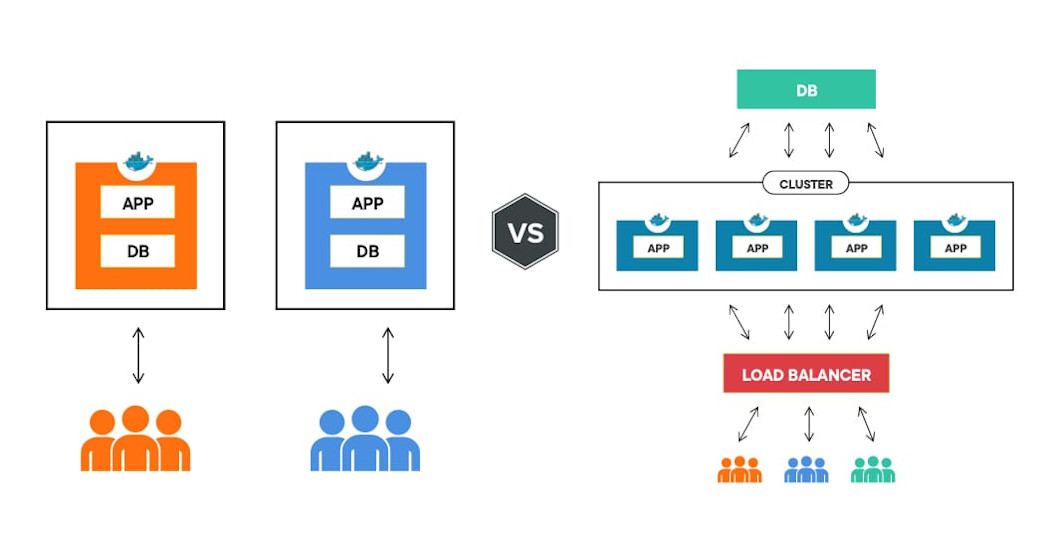
How to secure a multitenant application architecture
How to create and secure an application where multiple users share one account, are part of multiple organizations, and interact with other accounts.

Challenges building solutions for user sharable resources
Sharing resources between users seems like it should be simple, then why are there no obvious simple solutions? Maybe it isn't so simple after all.

Why companies gamble on user data privacy
Despite GDPR, we still hear about embarrassing data leaks, often at big tech companies. What is so difficult about protecting your users data? Turns out, it's just business...

OAuth Login should be standardized and this is why it cannot be
The problem of trust relationships in OAuth, how clients hold all the power, and why login/user identity should be standardized.
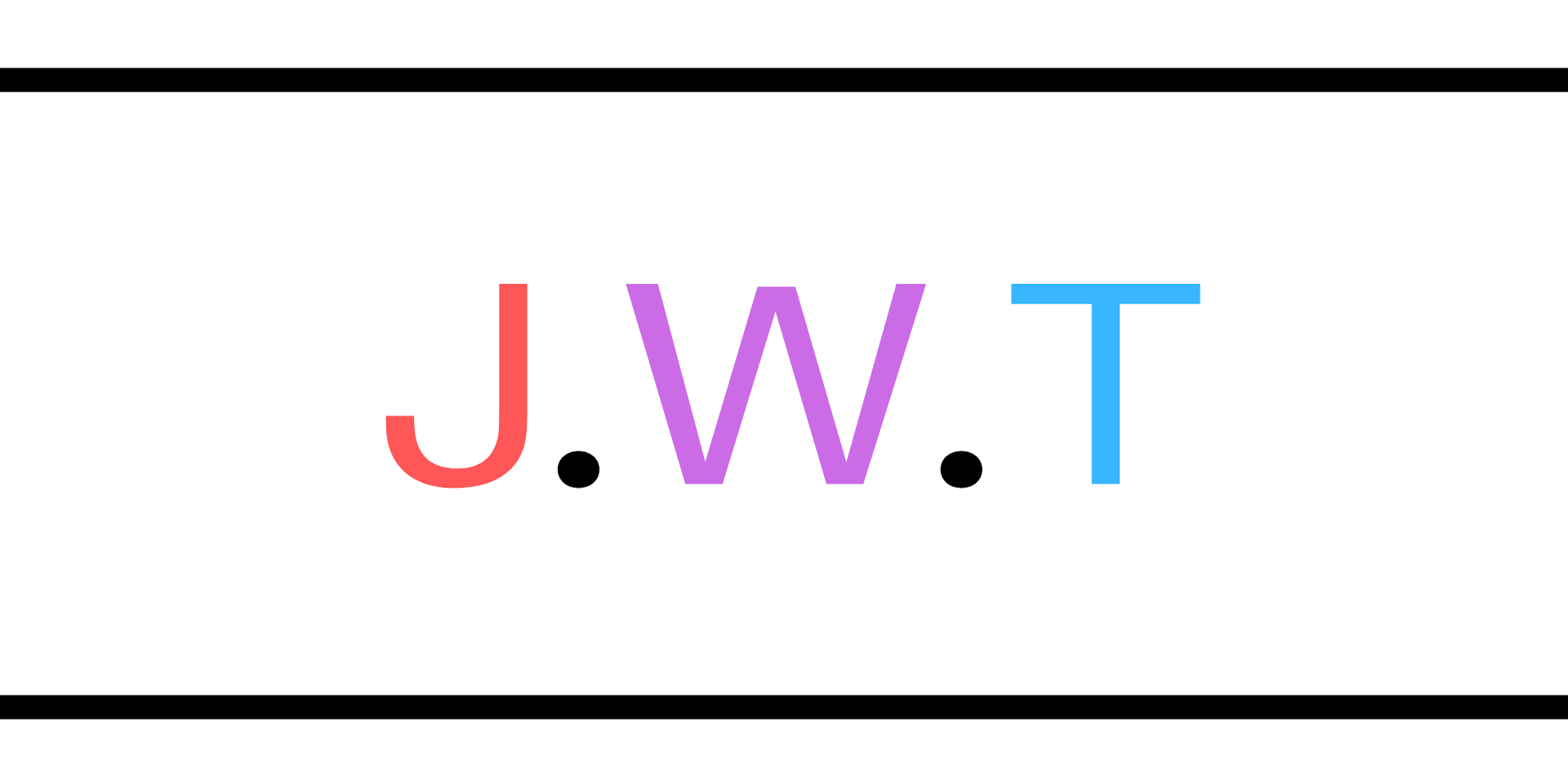
Validating JWTs in Web APIs
Securing a web application or api requires actually validating the access token that is being used. When using JWTs, there are two mechanisms for doing this.

Securely store client IDs and secret access keys
API access is provided through client IDs and secret access keys and because of the authority attached to these credentials they must be secured as safely as possible.

Choosing the right error code 401, 403, or 404
Here we’ll break down the most common HTTP error responses used for the purposes of API security.
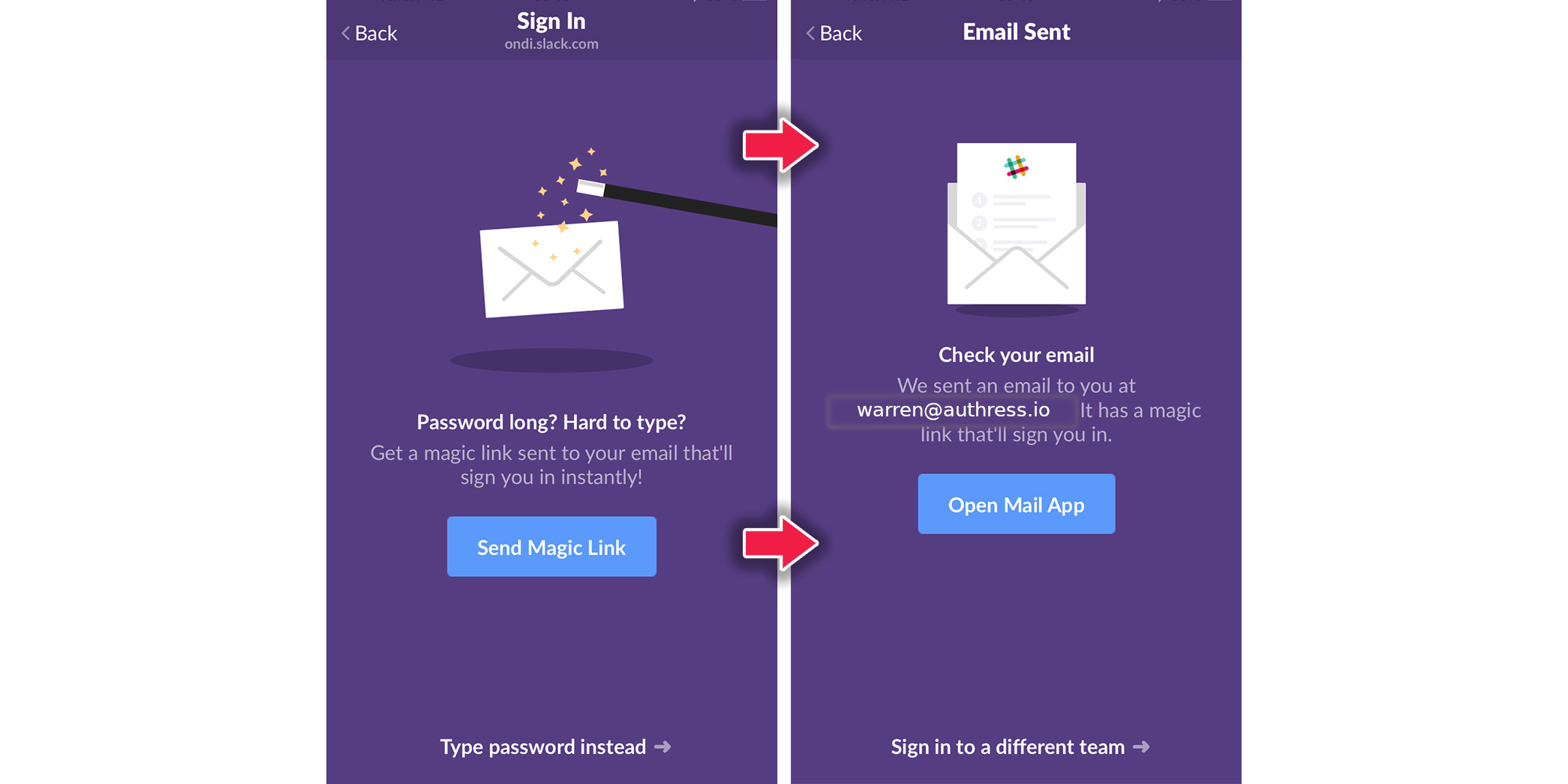
Magic links and Passwordless login
Making user signup and login easy is critical to having a successful app. Magic links and passwordless login helps, however it can create many problems longer term, and not ones that have easy solutions.

Handling security of long running transactions
A deep dive into security of long running offline transactions using refresh tokens and service client tokens.

JWT access token misconceptions
Tackling the myths of JWT roles at scale, what scopes are, and are CIAM providers expensive?
Videos

Slow and boring? Secrets to building reliable software

What the @#!? is Auth

Unintended consequences of well-meaning changes

Meeting Impossible SLAs: How we made our uptime 99.999%

Ensuring the reliability of Authress

Security or Convenience - Why Not Both?

Building a Security-First API

Why you should check your secrets into git

Adding Security to your Architecture

Build, buy, or use open source

How to estimate ROI on Security
Case studies

API Gateway Authorizers: Vulnerable By Design (Be Careful!)
API Gateway authorizers provide a unique opportunity to exposure yourself to malicious requests when defaults are used, and even when the defaults aren't used.

Are millions of accounts vulnerable due to Google's OAuth Flaw?
Are millions of accounts vulnerable due to Google's OAuth Flaw? It is certainly possible, but not the one that Truffle Security would have you believe.
AWS + Gitlab - Leveling up security of your CICD platform.
Stop using aws access keys and secrets today!

Zoombombing - a case study of data protection
Zoombombing is a relatively recent phenomenon, although underlying causes aren't new. In this case study, I take a look at what went wrong and how a company can protect itself from similar issues.