Authress supports authentication and authorization among other first-class features. Where possible, it is better to accept these identity providers through Authress using an Identity Connection.
However, you may wish to continue using your existing authentication provider with Authress when switching to Authress authentication is not possible. In these cases, because most identity providers do not support granular authorization and permissions management, it is a common augment your existing authentication and identity provider (IdP) with Authress Authorization and access control.
This configuration in Authress is called OIDC External Trusted Identities, and starting today, these identities can be used to generate custom user IDs.
Until now, when using an external trusted identity, the User ID was required to be the sub claim of the provider's generated JWTs. Now it can be any claim found in the JWT and that resultant User ID can also have a custom prefix.
This helps disambiguate different providers that have overlapping User ID spaces, allowing you to better restrict access to a single unique user ID.
Check out the new User ID Expression attribute available both through the API and in the Authress Management Portal:
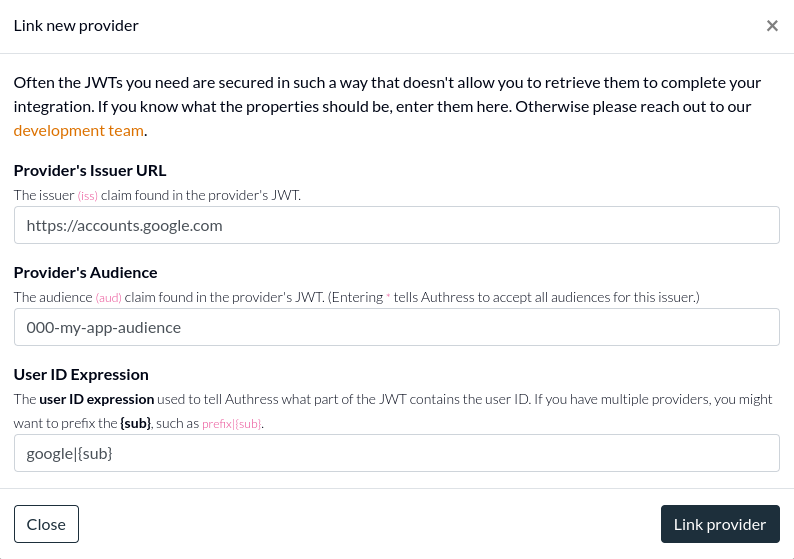
This configuration would generate a User ID google|1000-google-user-id.