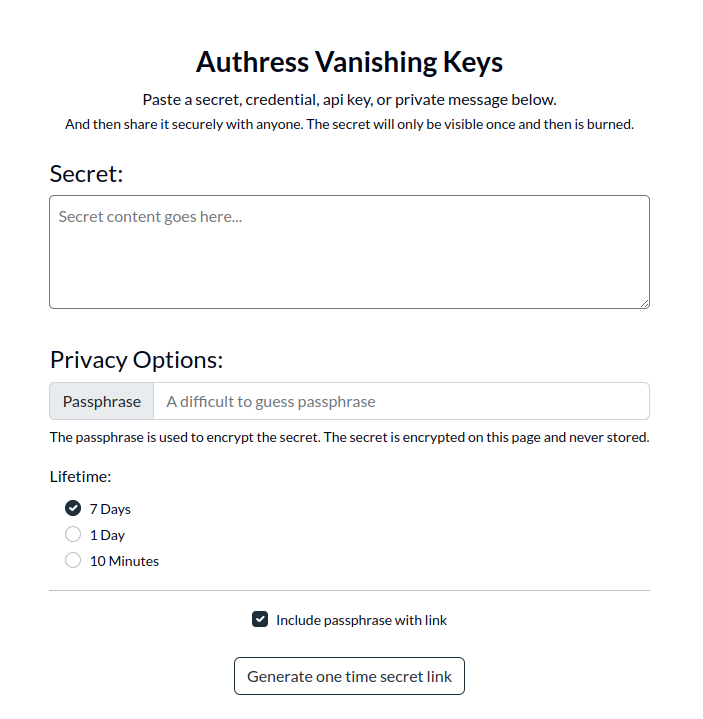
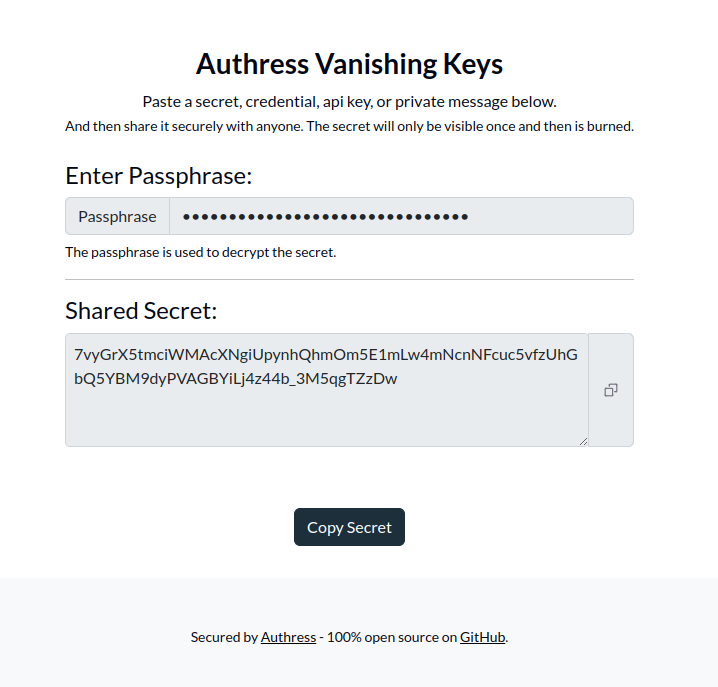
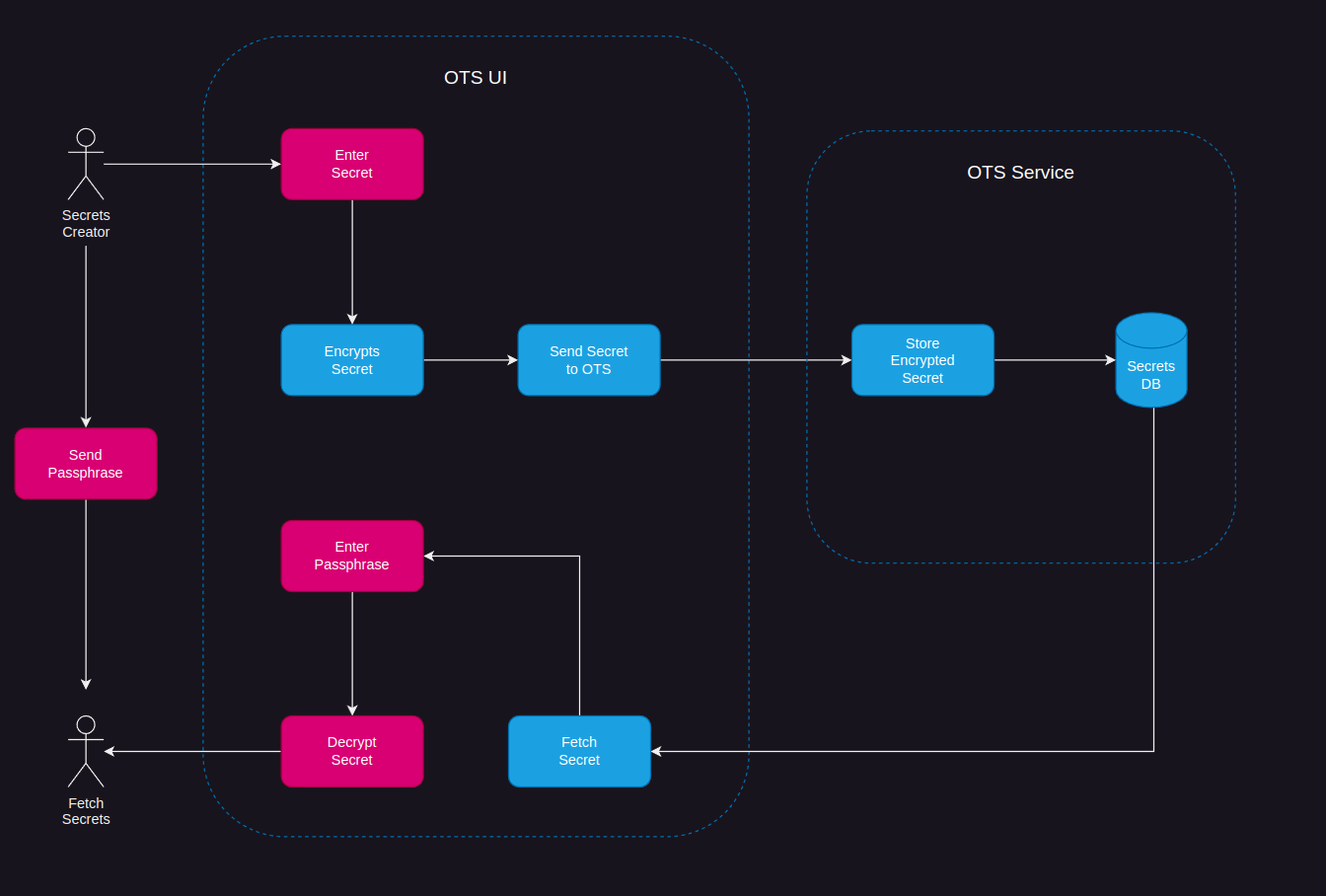
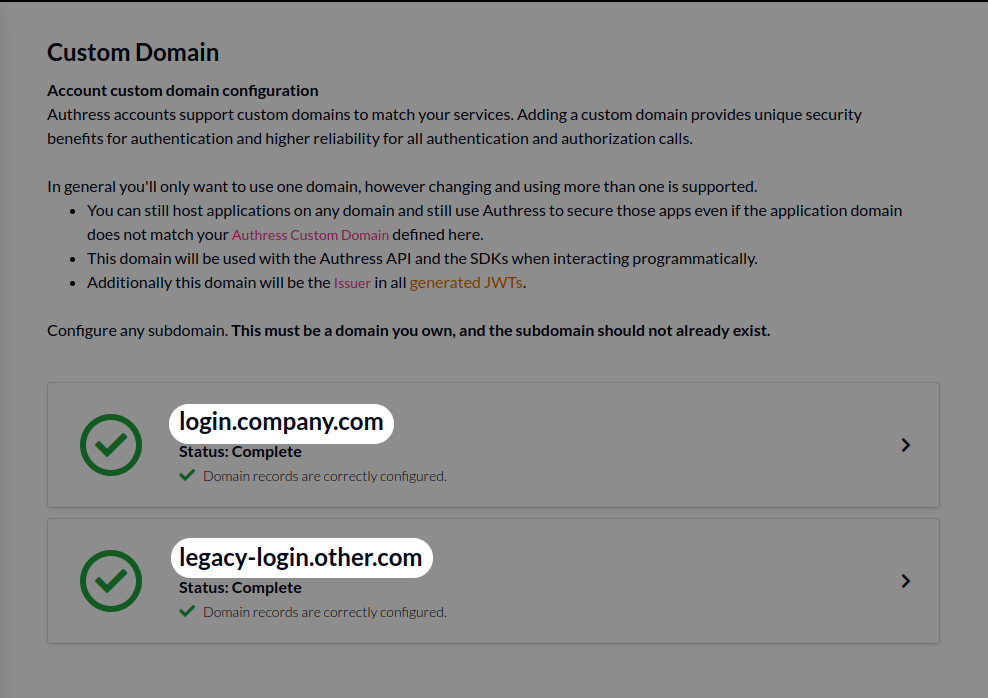
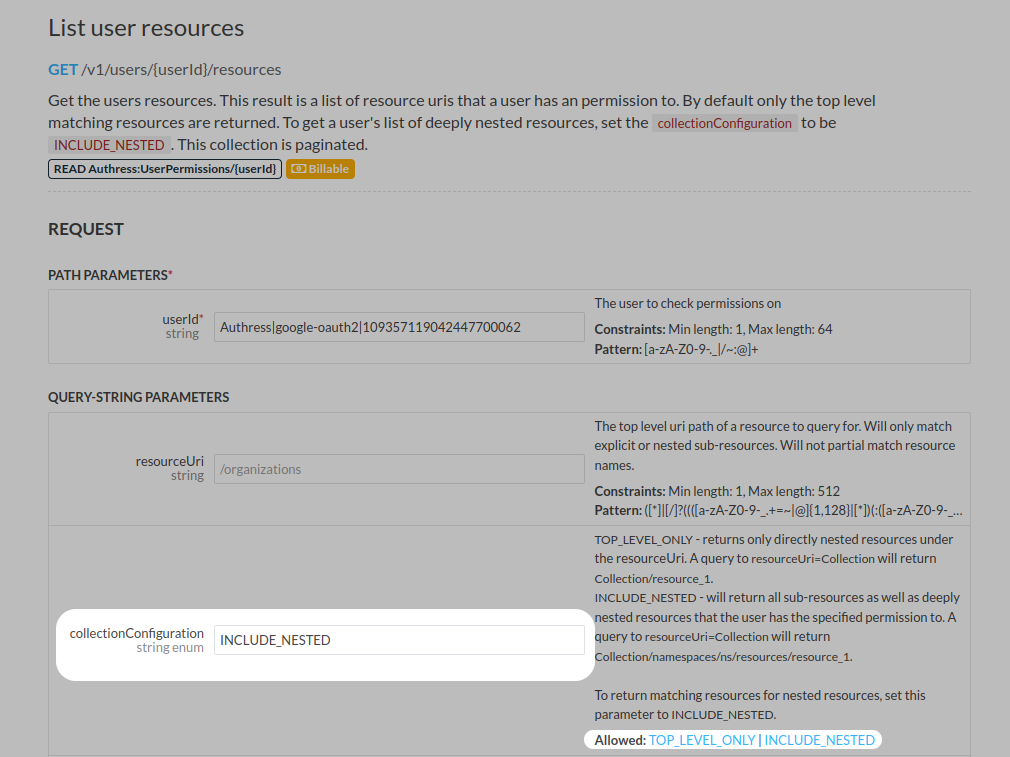
Link user identities automatically when the user signs up for a more seamless user experience. Starting today, Authress provides a new configuration option allowing for the automatic linking of user identities. When a user signs up with a new account, if that account identity passes our first level security checks and matches an already existing user identity saved in Authress, then Authress can link these.
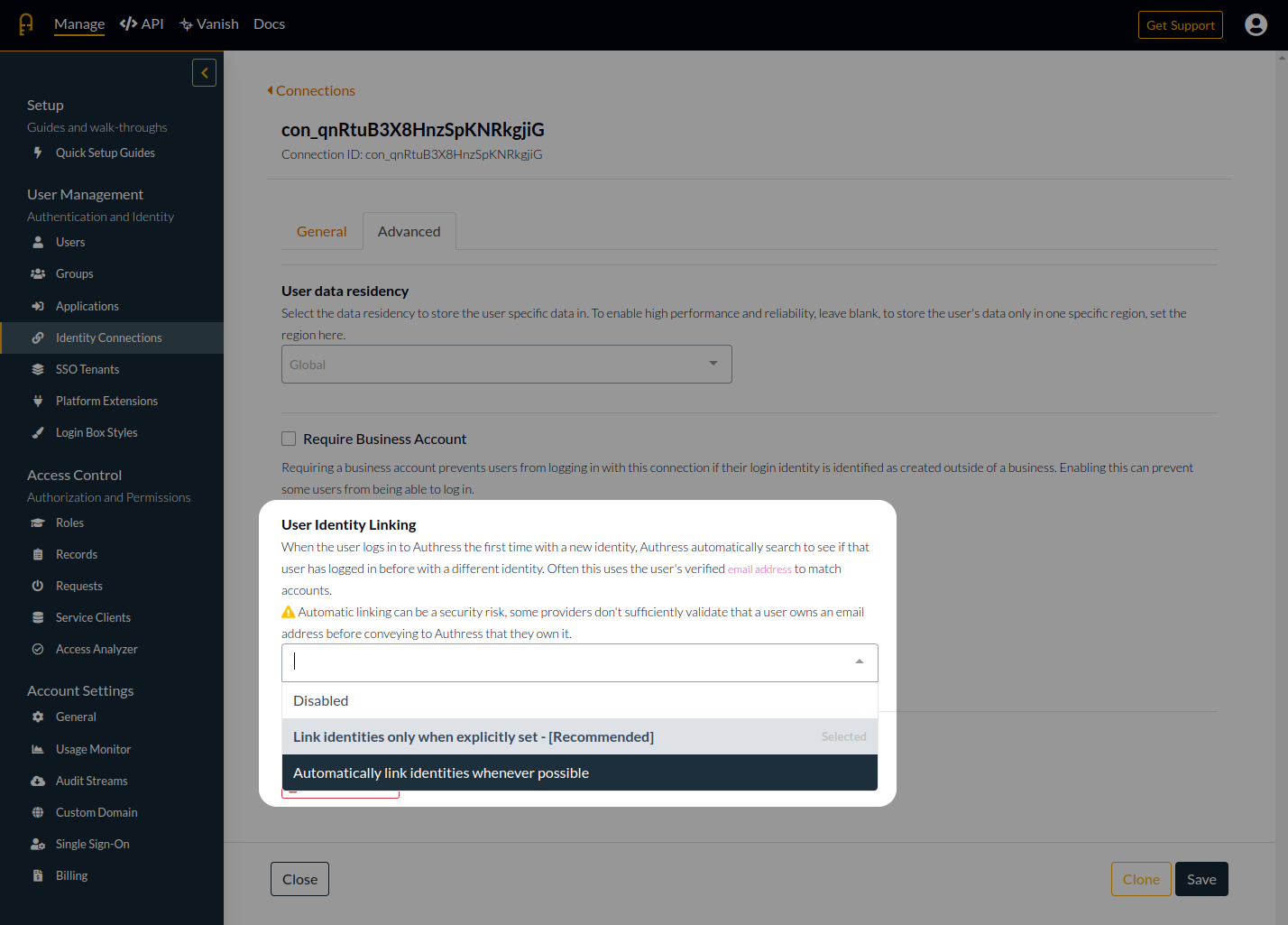
Linking identities
User identity linking supports the following three modes.
Disabled
Do not link identities and do not allow users to link identities manually. This options should be used by default in Business Contexts, when user identities and data is owned by a business.
Explicit
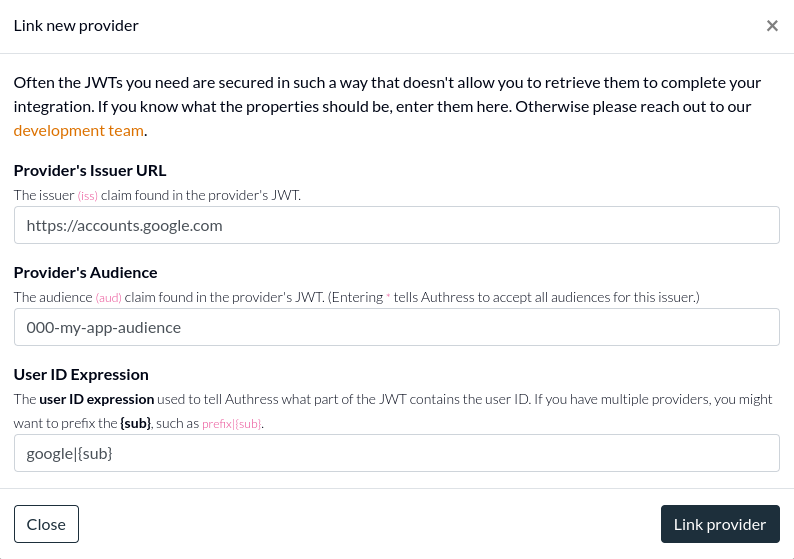
Allow users to link identities by utilizing the Link Identity API via loginClient.linkIdentity() call in the Authress Login SDK. More details about how to do this can be found under linking user identities in the Authress Knowledge Base.
Automatic
Authress will attempt to automatically link user identities when available. Authress will utilize the email address of the identities as well as other key properties to decide if it is safe to link. In the case that it is Authress will automatically link the identity.